60 Minutes & SS7 Signalling Security: Putting the Pieces Together
There was an interesting segment on the CBS TV program 60 minutes last night*. In this specific segment, the program covered what is possible through the misuse of the SS7 network protocol. What was demonstrated included tracking and interception of a phone that was leant to US Congressman Ted Lieu, as well as a discussion of what else was possible by attacking the SS7 network.
One discussion of interest was the use of these techniques by intelligence agencies, as it was stated in the program that:
The ability to intercept cellphone calls through the SS7 network is an open secret among the world’s intelligence agencies — -including ours — and they don’t necessarily want that hole plugged
This is a topical comment, but there are several sources of evidence pointing to the fact that intelligence agencies may be using SS7 techniques to track and monitor people:
- One, is that interception/tracking has already been detected and reported by Government state agencies, namely the Ukrainian secret service (SBU) as part of their investigation into suspicious, Russian-originated activity on their phone networks. This was in response to recent, political-themed call interceptions that had occurred on Ukrainian mobile networks. As an outcome of this, new legislation was submitted that one media source stated will allow Ukrainian security services to legally listen in turn to subscribers of foreign mobile operators
- A second is based on the activity that we have seen ourselves in our work with mobile operators worldwide in building defences to secure their networks. During the course of this, we uncovered several very sophisticated, global networks, engaged in the attempted tracking and interception of individuals in sensitive positions. As we have argued, the scale/sophistication and the objectives behind these lends themselves to believing that much of this is of an espionage/ spying function
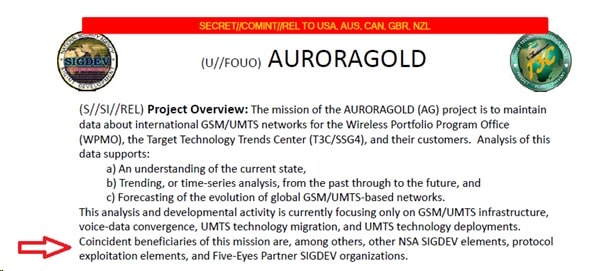
- But a third is the fact that we have some background material that has been released in various leaks, showing that some intelligence agencies have been collecting information to support attacks. One key piece of information, is that in late 2014, as part of the Snowdon revelations, there was the disclosure of a project called Auroragold within the NSA.
The main purposes of Auroragold is the collection of information on mobile operators. How this is achieved is through the interception and collection of what are called IR.21s, which are basically documents that mobile operators use to exchange with each, so their subscribers can interact and roam between networks, and allow networks to correctly bill each other.
The various leaked documents show that Auroragold focused on obtaining these documents in a variety of ways, and then making that information available internally. It was stated that the Aurorgold project gets this information in order for them to understand the current state of the networks, and predict trends for the future. However they also state that this information is of benefit to other SIGDEV (Signals Development) agencies within the NSA, protocol exploitation elements and partners.
Of interest to us, and why we focus on this, is that these IR.21s contain information on the configuration of SS7 networks within each operator – it order for other operators to bill and communicate successfully with it. Therefore collecting this information would be of use for any element seeking to exploit the SS7 protocol. It’s only a part of the story, and much more than an IR.21 is needed to execute a successful attack, but having this information helps gives a better picture of any network that an agency would want to attack. i.e. what mobile network elements are available, what types of subscriber and network numbers they use and so on. As we have seen from our own experience, attackers already ‘scan’ target operators for new network elements, and having the information contained in IR.21s helps them focus these attacks somewhat. When it comes to espionage every piece of information helps in executing successful attacks, and the authors of the slides clearly understood that exploitation elements would want to use their information. It stands to reason that this information would be used by SS7 exploitation systems if available.
The Norwegian Connection
Another comment from the 60 Minutes segment was that the average person is unlikely to be affected by this exploits or hacks. That is correct at a broad level. In our investigations it is not the ‘normal’ person that is being specifically targeted and hacked. But this does not mean they cannot be affected. This was demonstrated in a round-about, but spectacular fashion in the largest mobile network in Norway roughly 2 months ago.
On the morning of the 19th of February, over 1 million mobile subscribers of the Telenor Norway network found themselves with no cellular coverage for a period of 3 and a half hours, due to Telenor being the victim of an unexpected external SS7 ‘event’. As Telenor explained to the Norwegian regulator (Nkom) and to the public in a release on the 15th of April, they had received packets over the SS7 network from external sources that had caused a key part of their network – their HLR (Home Location Register) network element – to enter an ‘infinite loop’ due to the receipt of an unexpected packet format. The HLR is really the core database of the mobile network, and it being stuck in this infinite loop meant that activity ceased on the entire network for the over 1 million mobile subscribers it was responsible for.
According to the report that Telenor issued, the source of these SS7 packets was an operator in Luxembourg, who had been executing SS7 vulnerability analysis (determining if there was leakage of subscriber information) of other telecom operators in conjunction with a security consultancy. Whatever about the questionable nature of doing this analysis against another telecom operators and their critical network infrastructure in the first place without their consent, it certainly did not have the result that was expected. It was made clear in the subsequent statements that the technical fault on the Telenor side was due to the Ericsson supplied-HLR, which did not deal with the received packets correctly. Whatever the reasoning, or what was at fault, what this did show vividly is the wide-scale collateral damage that resulted from an unintentional SS7 event, and thus what could happen in the event of a deliberate and malicious attack on a network. As mentioned in the 60 segments program, all phones, regardless of type, rely on a functioning SS7 network, and if this is successfully attacked, critical elements of a nation’s infrastructure are at risk. In this case based on Telenor’s total subscriber counts, about one third of an entire network’s users did not have a phone service for many hours. Many of our examples on SS7 attacks that we have shown are stealthy location tracking or call interception attempts on potential high profile targets, but Denial-of-service attacks are also possible in theory, and as we have seen (inadvertently) in practice
Finally, one thing that was not covered in the 60 minute program, are the efforts that the mobile community is working on to address these flaws. It should be aware by people that there is an on-going activity within the mobile community to address these types of threats, and it is an effort that AdaptiveMobile has been leading since the beginning. It requires expertise and care, not only to deal with sophisticated adversaries that exploit these networks, but also to ensure that no ill effects comes upon networks in determining and implementing security. With so many people dependent on their mobile phone to communicate and work, building in security into the mobile network becomes more important every day.
*Disclaimer: AdaptiveMobile provided reference information to the producers of 60 Minutes/CBS for the purposes of explaining security in SS7 networks
