Potential Threat Vectors to 5G Infrastructure (9 Examples)
In our previous blog- ‘Is SMS still relevant in a 5G World and is it secure?’ we explained that 5G SMS relies heavily on the core network for legacy protocols and nodes. There are a huge range of SMS attacks and other forms of misuse that exist on networks today, and many misuses will continue to exist as the protocols and interfaces that enable SMS in 5G are the same. In this blog post, we examine what these attack types are and consider whether there are any novel attack types we might start seeing in new 5G mobile networks.
What cases of SMS misuse do we expect to continue in 5G?
We’ll see the following SMS misuse and messaging attacks continuing post 5G network deployment, as well as some new attack methods discussed later in this blog:
- Unsolicited SMS Messaging
- SMS Phishing (also called Smishing)
- Premium SMS Fraud
- Mobile Malware propagation via SMS
- Surveillance and Information Retrieval via SMS
- Denial of Service
- SMS Interception
- Grey Routes
- New 5G attack vectors
Let’s continue by looking at the purpose of these attacks, the way they work, and how 5G will affect them.
What is Unsolicited SMS Messaging?
Unsolicited SMS messages, or simply SMS spam, is the most basic yet most widespread method of attack using SMS. The purpose of unsolicited SMS is – like all spam – to make the recipient act on or otherwise engage with the message. Examples are aggressive marketing, adult content, fake prize giveaways or phishing attempts. The history of SMS spam has been nearly as long and widespread as the use of SMS itself. In the UK for example, the use of SMS exploded in the year 2000, but even then the dangers of unsolicited SMS was recognized. Since that time SMS spam has been a constant feature of mobile networks as the networks themselves have evolved from 2G to 3G and then to 4G. SMS spam is also highly adaptable, both in how it is sent and how it is presented. For example, when news of the Covid-19 pandemic first emerged in March 2020, spammers in North America quickly adapted to use it in their unsolicited messages.
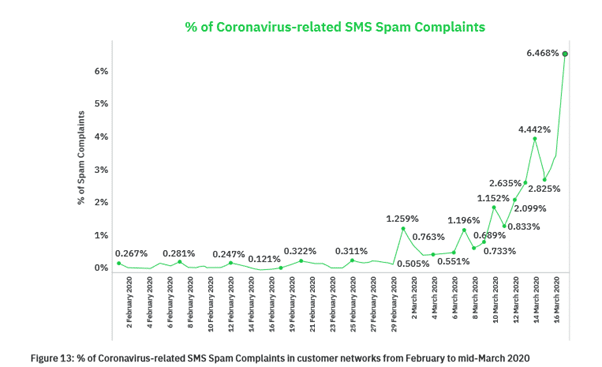
Are volumes of SMS spam growing?
The volumes of unsolicited SMS spam can be sizable and are increasing. To give some context, in 2013 we blocked roughly 100 million spam SMS in all our North American Operators. However, in January 2021 alone, in just one specific customer network in North America, AdaptiveMobile Security blocked more than a quarter of a billion (~317 million) spam SMS. Each one of these spam messages – if they had not been blocked – would have resulted in customer complaints, calls to customer care and potential financial damage to the mobile operators’ customers. The key to dealing with SMS spam is an active commitment by the mobile operator to detect and block SMS spam when it is encountered.
What is causing the increase in SMS Spam?
The driving factors behind this increase in SMS spam are both societal (people tend to react when they receive SMS messages), and economic (It has become increasingly easy to send these messages and the barrier for entry is becoming lower). In SMS we see this especially in the nature of where SMS spam comes from –in North America most of this SMS spam has come from VoIP/OTT carriers. These carriers allow people to connect using an account and quickly send SMS messages – bypassing the need to be in physical possession of a mobile device and so greatly expanding the number and scale of SMS messages that can be sent. From our analysis in the past, we found that a typical SMS from one of these VoIP/OTT carriers was hundreds of times more likely to be spam than a message sent from a handset on one of the traditional mobile operator networks.
Why will SMS Spam continue in 5G?
Given that 5G will still have the same paradigm of messages being sent from both ordinary mobile operators and VoIP/OTT carriers, we can expect SMS spam volumes and threats to continue into the 5G network. In fact, 5G may also expand the field of who can get access to large scale SMS sending methods. 5G networks will allow additional entities to make use of slices which would have access to the SMS sending infrastructure.
What are SMS Phishing Attacks?
SMS Phishing, also sometimes called smishing, is a specific type of unsolicited SMS Messaging, but we separate it out here due to its seriousness. It is often executed via a combination of social engineering and technical methods. In these attacks, the user receives an SMS which the attacker has tried to make appear as legitimate as possible by pretending to be a person/business or any other entity that they are not. Specific ways the attacker might do this is by:
- spoofing the sending number of a real entity,
- using a source number resembling a real entity,
- and/or using text which purports to come from the entity being spoofed.
Banks or other large enterprises where a fraudster can benefit financially by getting access are often a favorite target of SMS phishing. Below is a screenshot of one SMS phishing campaign in Ireland, where a Bank’s alphanumeric sending number was spoofed to seem more plausible. The first message in the thread was legitimate and from the Bank to the customer, but the second message is spoofed. Unfortunately, the handset is unable to tell the difference and places both in the same conversation.
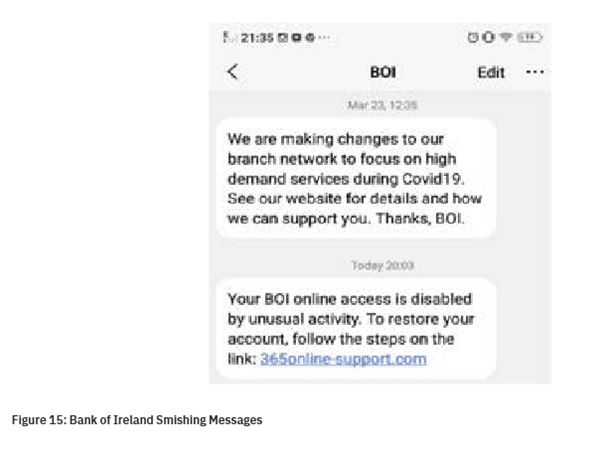
This is just one example and was made possible by Irish Mobile Operators’ lax approach to inspecting and blocking these messages. However, even in more secure networks, attackers don’t need to rely on that level of sophistication and have other social engineering tricks to use. In the US, we have monitored a specific gang that had been targeting smaller US Banks and Credit Unions over a long period of time. This group relied on targeting customers over weekends or around holiday periods to generate anxiety, and also because they knew that these smaller banks would be closed around this period. The attacker group used phone numbers rather than URLs in the text of the message, and they also often used a method called neighbour-spoofing – by using a sender number similar to the recipient and including a call-to-action in the body of the text message to dial a number which also looked similar to the recipient’s. This gives further credence to the message text, to encourage the recipient to ring the number in the message, to trust the attacker at the other end of the call and to possibly give them their personal details which could then be used for fraudulent activity.
Will SMS Phishing attacks continue in 5G?
We expect that the use of SMS phishing attacks will continue in 5G networks. In addition, faking or spoofing of the SMS source numbers will also continue to be possible in 5G networks. 5G SMS does not have any specific security enhancements for sender spoofing, especially for messages which are received inter-carrier. For further technical details on how SMS is transported by the 5G protocols please see our white paper Messaging for the Future: Securing SMS in 5G white paper. Overall, the conditions are in place for SMS Phishing to exist on SMS over 5G, in the same way it exists in all of the previous network generations.
Prevalence of Premium SMS Fraud in 5G
Premium Rate Numbers (PRN) are commonly used to provide a wide range of services, such as making donations, voting, gambling, adult services etc. PRNs can be SMS or voice based, that is, sending a text message or making a voice call to the Premium Rate Numbers normally costs more than a standard communication. Typically, this extra money is then taken from the sender’s account and given by the sender’s mobile operator to whoever runs the PRN. The PRN service provider may then pay a portion of that onwards to the third party, such as, for example, a charity, television show, or gambling service.
PRNs are often misused by SMS-using fraudsters, as a method to monetize their attacks. A common way is to infect mobile handsets with malware that will then send SMS messages to specific PRN ranges. There have been multiple examples of mobile malware monetizing itself using SMS to PRNs over the years, beginning with mobile malware for Symbian OS phones in the mid-2000s, before moving on to Android devices. Use of PRNs by malware remain popular to this day. Given that PRNs are a well-established feature of the global telecom infrastructure, and that the existence of mobile malware is also similarly entrenched, we expect that the malicious use of SMS to PRNs to monetize attacks will continue in 5G.
Mobile Malware Propagation
Mobile malware can use SMS for spreading, as well as monetizing, by sending messages from an infected phone which contain a link to a URL which itself links to the mobile malware. Social engineering is normally used to encourage the recipient to click on the link and download the mobile malware, which then continues the cycle by sending messages from the newly infected handset to more victims. This is termed worm behavior. The first SMS worm malware example for Android was Samsapo in 2014, which was quickly followed by Selfmite and then later that year by a worm version of the Koler ransomware . Since that time, the use of SMS by mobile malware as a worm distribution method was rare, until this year, when Flubot was detected in multiple countries. The Flubot virus uses spam SMS containing phishing text with information on parcel notifications, missed voice messages, etc., along with a URL link to the malware for its distribution.
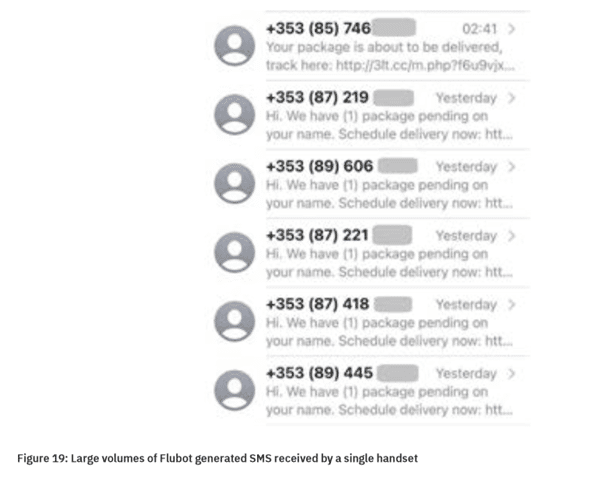
The attackers first targeted the UK and Germany, then added language packages for Italy and France, and the virus can now be seen further afield in countries like Switzerland, Norway, and New Zealand. Mobile Operators in these countries have struggled to block these attacks due to the malware’s sophistication, volumes, and the fact that SMS Spam detection and blocking is more advanced in some countries than others. Given the continuation of mobile malware into the 5G era, it is certainly technically possible that mobile malware could use SMS worm functionality to spread in 5G networks in the future.
Surveillance and Information Retrieval via SMS
While many of us are used to sending and receiving text messages from other people, there exists a whole class of SMS which are used to communicate to devices, processes, and machines. This type of non-human destined SMS is called binary SMS. Binary SMS are a special type of SMS designated to communicate directly to the Handset OS, UICC (SIM card) or application. In the past, attackers have used binary SMS to execute many different types of attacks on mobile devices and the SIM cards within them. One specific and far-reaching attack of this type is the Simjacker vulnerability, which was being used to track thousands of individuals in several countries before it was revealed by AdaptiveMobile Security in 2019. The Simjacker vulnerability exploited a specific library installed on SIM cards in some mobile operators, using it as an environment to execute specific commands without any user interaction.
The attackers sent specially formatted binary SMS to tens of thousands of victim handsets, which led to location and device information being obtained from the targeted subscribers. These attacks worked regardless of device type, i.e., Apple, Android, even IoT devices were being tracked using these SMSs. There are strong indications that the vulnerability is exploited by professional surveillance companies on behalf of nation-state(s).
Binary SMS is an integral part of the SMS environment of mobile operators nowadays, and it is expected it will also be used in 5G networks. In addition, UICC applications will still be used and managed in 5G networks, and binary SMS will be used to configure and control them. Therefore, binary SMS will still be used in 5G, and as a result, the possibility of binary SMS attacks will also continue to be present in 5G.
Denial of Service (DoS) Attacks via SMS
Location tracking and information retrieval are specific examples of the misuse of Binary SMS, but over the last 20 years many new types of Binary SMS attacks have led to Denial-of-Service type results, with descriptive names such as “SMS of Death” or “Curse of Silence”.
DoS attacks on a handset are designed to render the recipient device incapable of being used and/or unable to receive subsequent communications, either temporarily or permanently. DoS attacks do not need to use specific binary SMS messages or UICC cards. We have observed in the past how specific text strings in SMSs can perform denial of service attacks to crash handsets, such as the famous 2015 iPhone “Power” string attacks, which led to thousands of people in the US trying to crash iPhone handsets. Apple subsequently corrected the issue, but the potential will always exist that some sequence of characters sent over SMS may cause an issue, and this will continue into the 5G era.
Are Denial of Service (DoS) Attacks via SMS possible on 5G Networks?
DoS via SMS on handsets will still be possible in 5G. Based on the rate of new Binary SMS exploits over the last 20 years, our research indicates that on average 1.5 are discovered a year meaning that it is inevitable that new ones will be discovered in the future, and some of these will have DoS applications. Also, the fact that there will be an increase in IoT devices on 5G networks means that the potential to control and launch SMS DoS type attacks from large numbers of devices on handsets or infrastructure may be possible.
SMS Interception via signalling attacks
There have been multiple reports of sophisticated attackers that wish to access bank accounts. For this, they sometimes must break into the e-mail account of a user. A way to practically do this is to trigger the password reset mechanism, this is done via a one-time password (OTP) which is sent via SMS to the mobile device of the user.
Today, this SMS can be intercepted by mobile network signalling attacks that exploit the lack of security in the Signalling System No 7 (SS7), or the 4G Diameter protocol, both of which are used to communicate inside and between mobile core networks. The SMS interception attack uses the control plane signalling messages to redirect SMS to an attacker instead of delivering the SMS to the user. This kind of SMS interception attack was used by cyber criminals in 2017 as part of an attack to gain access to bank accounts in Germany, and more recently SMS interception via signalling attacks have been highlighted in Singapore, to gain access to credit cards.
While the network architectures are different between 5G and earlier networks, there is still the danger of attacks on 5G networks which could lead to the redirection and interception of SMS. Attacks on a 5G network, which change the subscriber related traffic routing information thus allowing the interception of the SMS, are potentially more difficult, but are still possible. These attacks could come from earlier 4G networks (due to the nature of inter-operability) or come from internal or external 5G networks over the roaming interconnect links.
5G introduced a new feature, called home-network control, or simply home-control. This feature ensures that the home network knows that the initial request for authentication from an outbound user is really coming from a roaming user. While this is a good feature, it is the responsibility of an operator to configure whether this check takes place only at the first authentication request of the user and what time-period it is valid for afterwards, or if it is checked for every authentication request. If it takes place only the first time and not for some period afterwards, then it may be possible for an attacker to force the home network to assume the subscriber is still present at the roaming network where they initially registered, and not a subsequent network. This could lead to a denial-of-service type effect. o prevent against this and other type of attacks, it is essential that 5G mobile networks are fully protected on the control plane, and that signalling messages are filtered to detect and stop these types of attack.
Grey Routes and Fraud SMS attacks
As we mentioned in our previous blog, SMS is now commonly for Application to Person (A2P) messaging, i.e. sending messages on behalf of companies or brands who wish to communicate with customers. Normally these messages are delivered via legitimate and agreed paths, which typically involve the sending party paying a certain amount of money to the receiving network. However sometimes these messages can be sent on a non-agreed path for monetary gain for the sender –This path is termed a grey route, which is a route to send a SMS between two parties that bypasses or does not travel via a commercially agreed path. As well as a loss of revenue for the receiving operators, grey routes are often executed using SIM boxes, non-secure senders, or poor-quality connections, leading to quality of service and security concerns.
In the past, we saw extreme examples, such as A2P messages being sent by an application that users were encouraged to download on their phone to earn money on. Termed “Bazuc”, as well as being against the operators’ terms and conditions, this application also meant that the content of these messages was accessible to the sending devices around the world (thus potentially revealing sensitive information). In addition, the App was also used to send SMS spam, putting the users of the App at risk of having their handset disconnected.
As A2P SMS will continue to exist in 5G, it can also be assumed, that less trustworthy A2P sending partners will continue to exist in the 5G interconnection ecosystem. Attackers could use SIM Boxes or identify non-monetized routes to inject and send A2P SMS to 5G network users, leading to financial losses to the recipient operator, but also risks to the message itself being sent via non-secure means.
What kind of new attack vectors might be possible using SMS in 5G?
It is difficult to foresee with certainty all the possible new attack types in 5G, but to recognize some, we could consider the new aspects of SMS in 5G. Looking at the 5G Network Architecture, one new aspect to consider from a security perspective is the introduction of the Short Message Service Function (SMSF). The SMSF provides the connection between the existing SMS infrastructure and the Service Based Architecture (SBA).
A new attack vector could be created when messages are sent directly to or from the SMSF. There are several ways this could be achieved:
- Through the roaming interface: For phones using 5G roaming, any text messages sent to or from the phone, would be converted to or from 2G, 3G or 4G, for use over the inter-operator interface. Essentially mobility control and registration would be handled by 5G protocols, but the sending or delivery of the SMS would be handled by one of the earlier protocols. Leaving potential security gaps and possible entry points for attackers.
- Through a compromised network function e.g., Access and Mobility Management Function (AMF) or in a compromised Slice. We can see several new ways that the SMS flow within 5G networks could be affected and some of the risks here are fraud and denial of SMS service. We have exposed Slicing vulnerabilities previously in our paper 5G Network Slicing Security in 5G Core Networks
- Via the Network Exposure Function (NEF) which also allows sending of SMS from an external party that uses the NEF to communicate with the core network. An SMS could be sent to the NEF from inside the 5G network, which would then relay this to an external Application Function (AF) which may be controlled by a 3rd party. It opens up another method in which SMS communications could be sent outbound from a mobile network, potentially leading to information loss.
What does the future hold for the security of SMS?
We can see that most of the existing SMS attacks on mobile networks today, unfortunately, remain pertinent on 5G networks. Furthermore, fraudsters who currently execute SMS attacks will look to see if there are any new methods, or attack vectors, which could use SMS in 5G networks. Trust is not a security strategy, and we must all learn from the lessons of 3G and 4G deployments. Mobile Operators must build in security from the start, based on best practices now, and what they may encounter in the future.
For a more detailed technical breakdown of all these new potential attack vectors in 5G please download our paper Messaging for the Future: Securing SMS in 5G