Simjacker SMS – Example and Frequently Asked Questions
Last week – on the 3rd of October – we presented on our research into Simjacker at VB2019. On that same day, we issued a technical paper on Simjacker, which is available here. This paper contains all the technical details about Simjacker, i.e. the Simjacker vulnerability, how it is being exploited, how the attackers have varied their attacks, as well as related attacks and technologies. As we have received a lot of questions over the last few weeks regarding Simjacker, we have created this blog to answer the most frequently asked questions. Further details on each of these points, and additional information, are available in the report.
1) What is the purpose of the attacks/ How is the attack executed
The primary goal of the attacks is to retrieve Location information (serving Cell ID) and device information from targeted mobile phone users. An example of one of these attacks is below. Occasionally, other functionalities like displaying text, opening up a web page or various forms of testing are executed by the attackers, an example of the browser being opened is also below. The attack is normally done by sending a specific kind of SMS to the targeted mobile subscriber. The contents of this SMS, which are a set of instructions, are then executed by the SIM Card within the subscriber’s mobile handset. In this case, the SIM Card runs the instructions by retrieving the location and type of the mobile handset, from the handset, and sending another SMS back to the attacker, which contains the retrieved information, all without any indication to the user.
For more information – Simjacker Technical Report: Section 3 & Section 4(report)
Example of Location (Cell-ID retrieval) , victim handset is currently roaming in Ireland (MCC=272) and on Irish Mobile Operator (MNC=01 VF Ireland). Note: VF Ireland are the roamed-to operator for the vulnerable SIM, they are not the vulnerable operator. Note: ~5 second SMS transmission delay removed.
Example of Browser(s) being opened automatically by sending instructions. 3 websites are instructed to be opened within a new browser window. Such a method could be used (in conjunction with a handset vulnerability if one was known) to download mobile malware onto a handset from an infected website. Note: ~5 second SMS transmission delay removed.
2) Who is being targeted/Am I being targeted:
It is highly unlikely. As the report outlines, we have detected hundreds of mobile subscribers per day being targeted, but we have only detected the Simjacker vulnerability being exploited against subscribers from 3 countries – Mexico, Colombia and Peru so far. Also, the threat actor that we observed using this exploit generally sells it to nation-state customers. The ‘average’ person is not likely to be targeted, and like SS7, the primary targets are probably those that are of interest to nation-state customers.
For more information – Simjacker Technical Report: Section 4 & Section 6 (report).
3) Is my phone vulnerable/Isn’t this an old, unused technology?
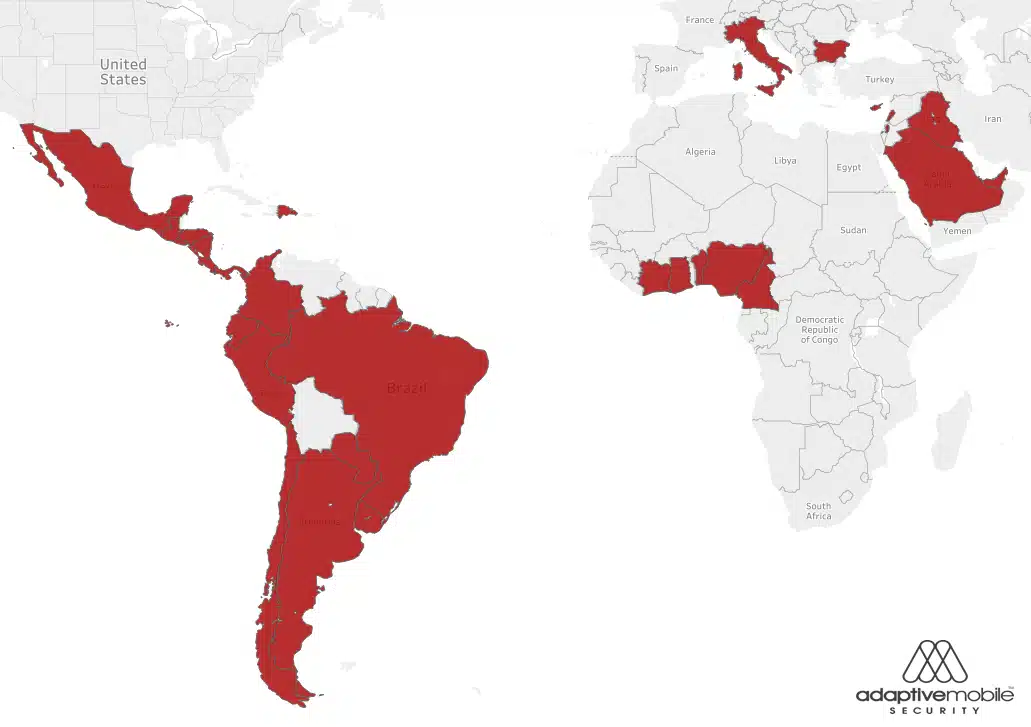
The attack targets SIM Cards which contain a technology called the S@T Browser. The S@T Browser technology is used in at least 61 mobile operators, in at least 29 countries. A map is available in our report (and below) of what countries we believe still use the technology. As we also specify in our report, the most probable, conservative estimate is that mid to high hundreds of millions of SIM Cards globally are affected. While the S@T Browser specification may not have been updated since 2009 until now, it is still widely deployed. The SIM Card technology itself is independent of handset type, i.e. Android, iPhone, IoT type devices are all vulnerable if their embedded SIM Card uses the technology.
For more information – Simjacker Technical Report: Section 7 & Section 3 (report).
Map of Countries where there are 1 or more Mobile Operators actively using S@T Browser on SIM Cards with no-security level set.
4) How can I protect myself
Unfortunately, there is very little that a person can do to protect themselves. There are tools that you can download to determine whether your SIM card is vulnerable (with special equipment), or potentially tell you if you are being targeted (but requires a rooted device). However, these tools do nothing to protect the user. The only entities that can put protection in place for targeted subscribers are the mobile operators. Their options are to change the security settings on the SIM Cards, and/or put special filtering in place to prevent the SMS from exploiting the Simjacker vulnerability being received by targeted mobile subscribers.
For more information – Simjacker Technical Report: Section 8 (report).
5) Why is the S@T Browser technology vulnerable?
The S@T Browser technology is vulnerable due to an apparent oversight in the S@T Browser specification. There are 4 different ‘protocols’ (commands) defined within the S@T Browser, and security levels recommended for them. However, the commands used in these attacks: Push messages, didn’t have any security level associated with them. This lack of a recommendation or specification meant that no security was associated with these commands in practice and that any source could send a S@T Browser message that would run on the SIM card with no authentication.
For more information – Simjacker Technical Report: Section 3 (report).
6) Was this vulnerability reported before?
Not to our knowledge. The Simjacker vulnerability Enea AdaptiveMobile Security reported as being exploited is in a specific SIM card technology called the S@T Browser. The S@T Browser is being exploited via specific SMSs called SIM OTA SMS (although other ways of attacking the SIM are possible). Previous publicly revealed research has shown how these kinds of SMS can be used to execute other unwanted functionalities around SIM Cards – examples include triggering an automated response or obtaining a SIM DES key, and in fact, the potential for misuse of SIM OTA SMS had been discussed within the industry even before these. However, the specific Simjacker vulnerability we reported is the misuse of the S@T Browser environment, not the misuse of SIM OTA SMS.
The closest previously publicly reported research would have been specific exploits attributed to the NSA TAO team which also obtained location information, but these are stated as requiring OTA keys, and so are highly unlikely to have used the S@T Browser vulnerability. The fact that the vulnerability is being actively exploited has also not been reported before.
For more information – Simjacker Technical Report: Section 3 & Appendix A (report).
7) What is being done to block these attacks
Within the GSMA Association, specific information from AdaptiveMobile and the GSMA has been distributed for some time on the vulnerability and the best ways to prevent and block these attacks. In addition, the SIMalliance made some updates to its S@T browser specifications to improve the security of these applications. Taken together these have the potential to greatly reduce the risk of the attacks being successful.
One important aspect highlighted in the report is the sheer range of evasion techniques deployed by these particular threat actors. The attackers have been executing highly complex functionality that many mobile operators would not have considered when putting in place previous recommendations. To defend against these attacks, Mobile Operators – to be safe – would need to be far more vigilant in their day to day security.
For more information – Simjacker Technical Report: Section 8 & Section 4 (report).
8) How come you are only releasing the details now?
A limited amount of public information was released initially on the 12th of September, 2019. However, in the background, technical details had been shared with the GSM Association as part of a Co-ordinated Vulnerability Disclosure (CVD) process since late June 2019, for mobile operators to act upon. Mobile operators are essentially the only entities who can effectively stop these attacks which is why the focus was on sharing information with them and alerting them first in a responsible manner.
For more information – Simjacker Technical Report: Section 2 (report).
9) Who is the company you believe to be responsible?
Within the report, we outline why we think it is a surveillance company that developed this exploit. However, we have not named the specific company that we believe is responsible, as to do so, we would need to release some additional proof. That proof would also reveal specific methods and information that would impact our ability to protect subscribers. The actual identity of the exploit developer is not essential to know when planning how to defend against these types of exploits. We know that it has been used by a threat actor who executes highly sophisticated and complex attacks, so mobile operators should expect them to adapt quickly to any defences and try new techniques in the future.
For more information – Simjacker Technical Report: Section 6 (report).
10) What about other SIM Card technologies like WIB?
WIB is a propriety SIM card technology like S@T which reports show could also be exploited via ‘Simjacker-like’ attacks. However, it’s important to state that we haven’t seen any attacks involving WIB. The WIB technology itself seems less prevalent than the S@T Browser (see diagram below and section 7 of the report), and publicly available information doesn’t indicate that WIB has the same apparent oversight in recommended security level. However, this is an area of continued research, as well as whether there are any other vulnerable SIM card technologies, and if they can be exploited.
For more information – Simjacker Technical Report: Section 7 (report).
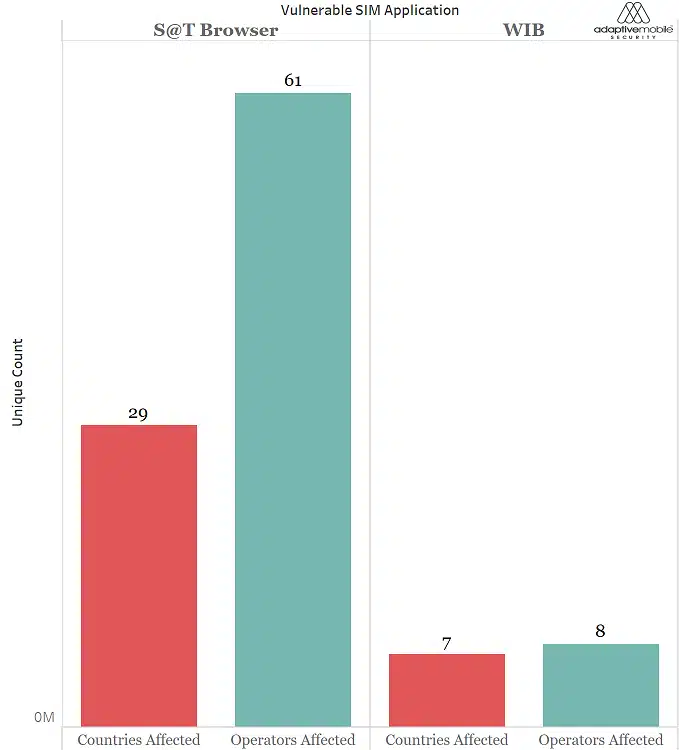
Count of Vulnerable Countries & Operators for S@T Browser and WIB
If you are interested in the topic of mobile surveillance, and want to do some further reading, start with this post detailing how surveillance companies track people using mobile networks.