DoneDeal PayPal Phishing Scam
Caveat emptor – “let the buyer beware” – is an age-old law of commercial transactions. Online, sellers need to be on their guard too. While the typical text message scam involves ‘phishing’ for information, this scam involves fishing for something far more tangible: valuable items that will be easy to dispose of for cash.
DoneDeal scam: a different kind of phishing
DoneDeal is an online marketplace based in Ireland specialising in cars and personal trade ads. While some sellers offer to ship, the most common way of exchanging goods is in person. Sellers are encouraged to provide a verified cell phone number to give some reassurance to potential buyers.
How does a DoneDeal phishing scam work?
Armed with a contact number and information on what valuables are available, the scam begins with a text message:
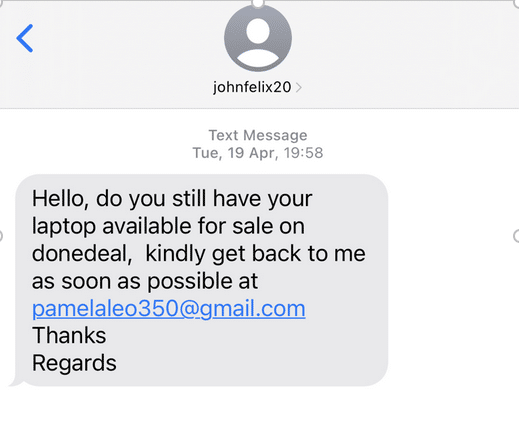
By using a text message to initiate contact, the scammer has taken the conversation off the marketplace website where suspicion may have been aroused and the account cancelled. Furthermore, by exploiting a weakness in the receiving network that allows labelling the message with a fake sender (here “johnfelix20”) they force the seller to move to email to continue the conversation.
PayPal according to Pamela
Safely out of sight of both the selling platform and the mobile network’s scam defences, the real business can begin.
After some negotiation about condition and price etc., “Pamela” reveals she won’t be able to view the item at this time but is happy to take it as soon as possible. She will pay by PayPal and would like the laptop shipped to her home address in Spain as it is a gift for her daughter.
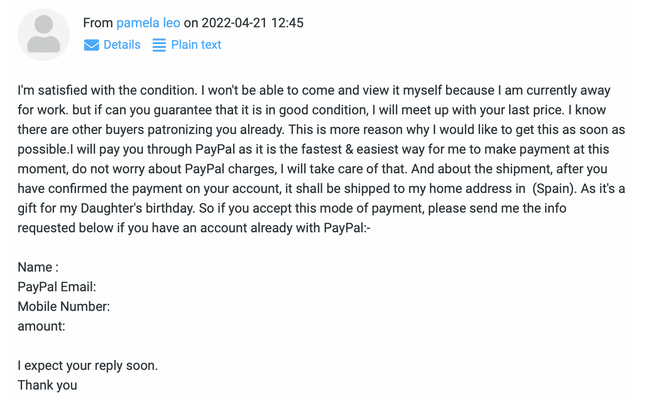
After we respond to agree to these conditions, the mainstay of the scam arrives later that day.

While most email providers will have their own spam filtering, a quick examination of this email’s headers shows it has slipped past the defences this time:
X-Spam-Status: No X-MailScanner-SpamCheck: not spam, SpamAssassin (not cached, score=2.3, required 4)
Email spam filtering is based on a “score” calculated from multiple features of the message. While this message collected some points for suspicious attributes, its score of 2.3 was below the threshold to be considered spam. On another provider on another day the message may have ended up in the spam folder, however “check your spam folder” has become such a frequent suggestion even from the safest of senders, finding an email there is no longer in itself a deal breaker.
So, it falls now on the evidence of our own eyes and intuition to decide whether this message is legitimate.
If the PayPal branding looks convincing, it should; the graphics are loaded directly from PayPal’s real website. But before we start spending any of this imaginary money, this email needs much closer inspection.
How to spot a fake PayPal email
1. Check the email address
The email came from: Notification of Payment <[email protected]>
Depending on the software used to read an email, the sender’s address might not be immediately visible. As the scam involves interaction with fake PayPal, the scammer was obliged to use an email address they can control. In this case “paymentaccts.com” Is hosted on Google for the purposes of sending and receiving email. There is no website at that address.
2. Poor writing abounds
The email tells us that “Payment On Pending” which makes no sense, and uses tenses poorly: “you would have to ship the item.” Standardized business to customer emails like this one, which in theory would go out to the thousands of customers who transfer funds using PayPal, are not typed out on a whim, containing obvious grammatical errors. Poor grammar should always raise a red flag.
3. Urgent tone
Considering it should just be transferring funds from one account to another, the fake PayPal is far too invested in this transaction. The email has two goals:
(1) Reassure me, repeatedly, that I am really going to get the funds.
(2) Make sure I post the item as soon as possible.
All that remains is for the seller to post the item. To put off suspicion a little longer however, fake “PayPal” confirms proof of sending, and lets me know that the “immediate” release of funds may now take an additional 48-72 hours.
How do you sell online safely?
Despite the rough quality of the emails, the scammer used some effective strategies:
- By appearing to borrow the credibility of PayPal, the scammer does not need to convince the buyer that she is trustworthy. If one believes the emails are genuine, then one must only trust the credibility of globally recognised PayPal.
- The emails would not convince an experienced seller, but someone unfamiliar with interacting with online payments may be convinced by the legitimate logos. The scammer cleverly included links to ask for help and support, all directing back to the same email address.
- The scammer persuades the seller to ship overseas, knowing the chances of follow up or recovery of the goods is virtually nil.
Selling online is a skill and a profession. If you’re just offloading your old laptop, mobile phone, or other re-sellable item, take some simple precautions:
(a) Do not entertain any unusual requests. Genuine buyers will want to see the item and are unlikely to go looking overseas for easily available items.
(b) Do not accept any unusual payment methods. Confirm receipt of funds before handing over or shipping any item.
(c) If possible, conduct the business in person, in a public place.
How can operators help?
Subscribers will usually default to trusting the sender information they see on their phone screen, assuming that this is information provided by their mobile network.
However, in the complex ecosystem of modern texting, messages come from many sources. CPaaS (Communications Platform as a Service) companies, which provide their clients an entry point to mobile networks, should exercise control over the sender information provided, with a suitably configured messaging firewall. Operators in turn should require restrictions on sender information as a pre-requisite for access to their network.
Contact us to learn how ENEA AdaptiveMobile Security has implemented originator address checking for CPaaS providers operating across Europe, the Americas and Asia Pacific.