HXXP Malware Spread By Fake Russian MMS & SMS
MMS 9560 “I love you” fake MMS notification
Android premium rate SMS Trojans (aka toll fraud) is nothing new in Russia but typically it is distributed via fake Android marketplaces or unofficial app stores. In conjunction with one of our carriers customers we investigated malware that was promoted via SMS. In this attack spammers were targeting Russian consumers with a social engineering campaign that sent out tens of thousands of SMS with links to a website hosting mobile malware.
Distribution
This threat was promoted via SMS instead of Google Play or the fake Android markets that have been seen before in Russia. Since Google increased the security of Google Play scammers have gone off market looking for other channels to distribute and promote their apps to a wide audience.
The SMS tell the recipients they have received an MMS message with the text “I love you” and a link to view the MMS.
“Vam prishlo MMS s tekstom “Anastasiya, ya tebya lublu!”. Prosmotr: hxxp://mmsget.org/9560.htm”
The name in the SMS varies but is usually a woman’s name. It is an interesting use of social engineering to entice people to click on the link.
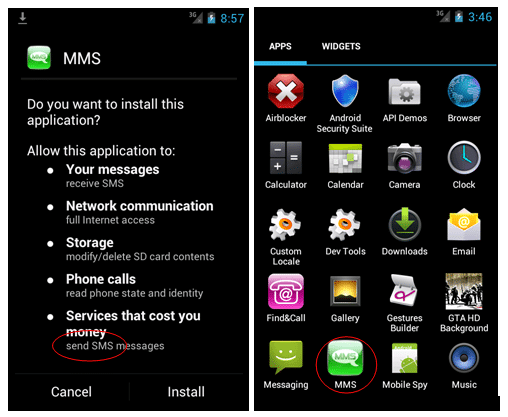
If the link is clicked on using an Android phone it downloads an SMS Trojan app that sends out 5 premium SMS without notifying the user. The malware is a variant of the FakePlayer family. If a phone that supports J2ME is used it downloads a variant of the J2ME.OpFake family.
Infection
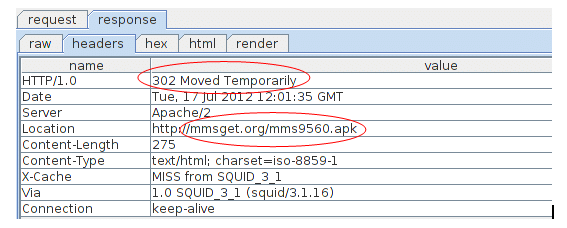
The app is downloaded through a “drive-by download” technique. When a subscriber clicks on the link hxxp://mmsget.org/9560.html using an Android browser the malware app is downloaded automatically without user intervention. The malware authors achieve this by configuring the server to send a HTTP 302 response to the browser that links to the malicious apk. This causes the browser to issue a GET request for the apk that is downloaded to the phone’s file system without the user’s consent.
Drive by download
The app is a variant of the FakePlayer family that was first seen in August 2010. If a non-Android phone is used a J2ME file, mms9560.jar, is downloaded. This is a J2ME.Opfake variant.
Several URLs have been identified as serving up malware from Russian servers:
hxxp://mmsget.org/9560.html -> hxxp://mmsget.org/mms9560.apk
hxxp://mmsrus.ru/9560.html -> hxxp://mmsrus.ru/mms9560.apk
hxxp://mmscom.ru/9560.html -> hxxp://mmscom.ru/mms9560.apk
The URL names are similar to ones use by Russian operators and have been chosen so the user thinks they are going to a legitimate website to view a new MMS that was sent to them.
When the download starts, the phone shows a notification.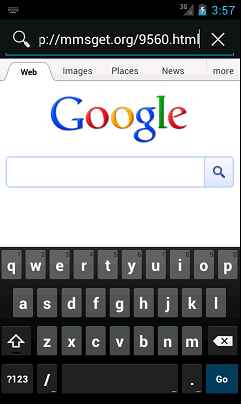
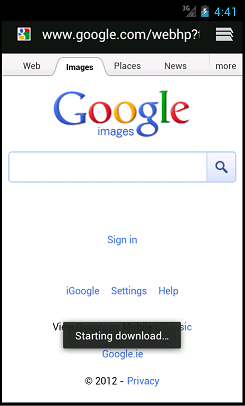
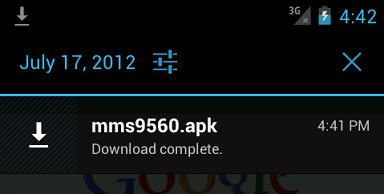
After the app has downloaded the user has to click on it to start the install – it does not install automatically without user intervention. The app puts an ‘MMS’ icon on the desktop.
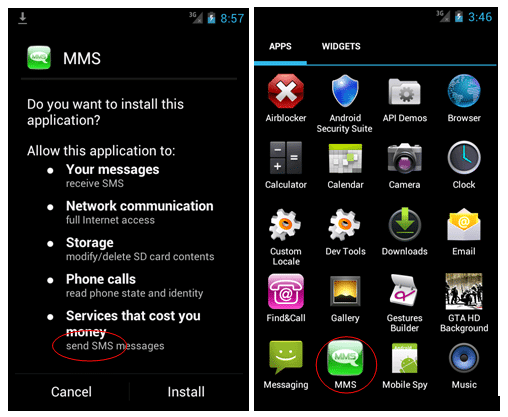
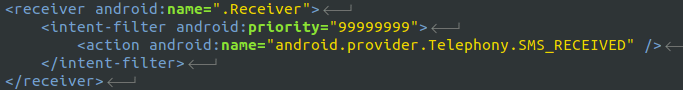
The app starts a background receiver to intercept any SMS replies from the short codes so that the user does not know that they have been charged as the SMS will not show up in the Inbox.
When the app is opened it immediately sends out 5 SMS to premium short codes while showing a loading screen. The SMS numbers and contents are read from a configuration file inside the apk package.
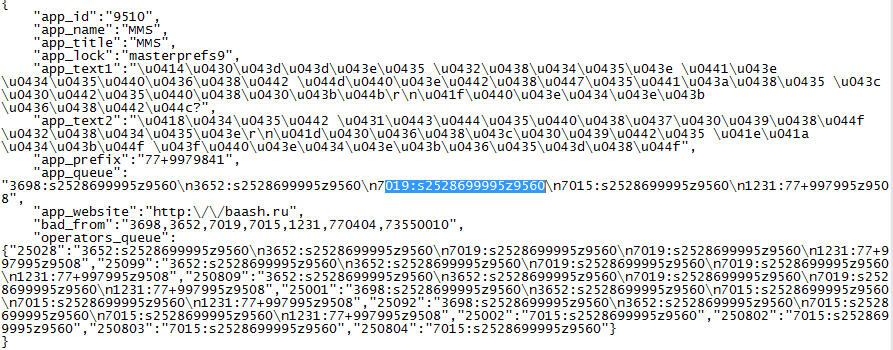
The text may be related to the original FakePlayer app and left in by the author.
app_text1 Данное видео содержит эротические материалыrn Продолжить?
app_text2 Идет буферизайия видеоrnНажимайте ОК для продолжения
The app_id value is not used in the app, the ‘9510’ value may refer to an earlier version of the threat that used a different URL such as
hxxp://mts-mmsru.ru/9510.html
hxxp://91.202.244.25/9510.apk
hxxp://mtsport.ru/9510.html
Sending premium SMS
As the SMS are sent, they can be seen in the debug log.
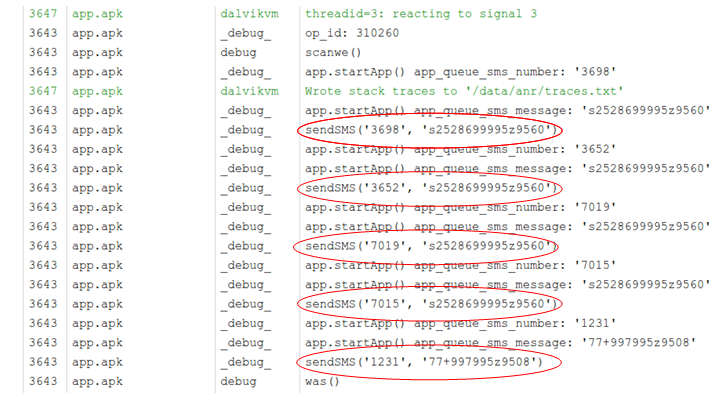
After sending out the SMS, the app displays the fake MMS to the user in a webview that loads content from the website ‘hxxp://baash.ru/’.
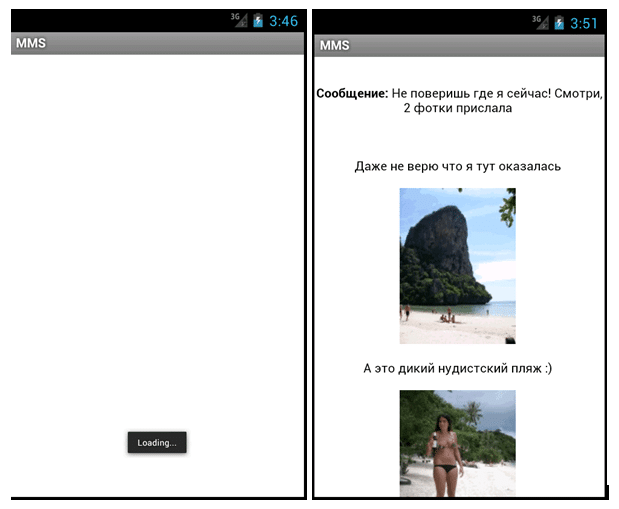
The 3 lines of the MMS says:
Message: You won’t believe where I am now! Look at the 2 photos I sent you.
I can’t believe I am here.
This is a new nudist beach
Premium SMS
The 5 short codes used by the malware will only affect Russian subscribers as they are only valid in Russia.
3698 costs 300 roubles per SMS sent
3652 costs 200 roubles per SMS sent
7019 costs 80 roubles per SMS sent
7015 costs 35 roubles per SMS sent
1231 costs 4 roubles per SMS sent
The 5 SMS sent by the app will cost the subscriber approximately 619 roubles (15 Euros / 13 GBP / 20 USD). The exact cost may vary per network.
Source of SMS
The app does not attempt to promote itself via SMS so this malware is not the source of the fake MMS notification sent to Russian subscribers. There is evidence of SMS being sent from multiple countries into Russia, as well from Russian mobile numbers.
+673 Brunei
+84 Vietnam
+230 Mauritius
+995 Georgia
+249 Sudan
+628 Indonesia
+234 Nigeria
At this moment it is unclear what is sending the SMS – they could be sent by malware from infected phones or by scammers sending an SMS spam campaign.
History
There is evidence to suggest that there may have been earlier versions of this scam, using different URLs. Note that the URLs are designed to look like legitimate URLs used by Russian operators.
hxxp://mmscom.ru/9503.html
hxxp://mms4you.ru/9540.html
hxxp://mts-mmsru.ru/9510.html
hxxp://mtsport.ru/9510.html
hxxp://mtsport.ru/9510.jar
hxxp://www.megafon-mms-portal.ru/9511
hxxp://mmsportal-mts.ru/9511.apk
hxxp://mmsportal-mts.ru/9512.html
hxxp://beelineportal-mms.ru/9509.html
Some of the URLs served up both J2ME and Android premium SMS Trojans.
It is unclear exactly how many phones were infected in this the “9560” campaign, most likely in the low thousands, but it and it’s predecessors were successful enough for the authors to start working on new variations which we’ll cover in a follow up posting.
Summary
Although these scams are most prevalent in Russia, we’ve seen a number of copycat compound threats, using SMS and social engineering to deliver mobile malware to users phones appearing across the globe. Whilst many operators already have measures in place to counter SMS spam, it is important that they are aware of these specific threats so that they ensure the correct action is taken to protect consumers.
Thanks to Yicheng Zhou for assisting in the analysis of the samples.