How Surveillance Companies track you using SS7 on Mobile Networks
Surveillance companies are often in the news, but the month of December, especially, brought three impactful headlines, which all related to how surveillance companies are using mobile networks to track you. So, the talk that Cathal Mc Daid, CTO of AdaptiveMobile Security, gave at the RC3 conference on 30 December could not have come at a better time.
Exploitable vulnerabilities in mobile core signalling networks have been known to exist for many years. However, very little information has been presented on whether these vulnerabilities are being exploited in real-life or not, and if so, how it is being done.
“Watching the watchers” presentation covers how there are 3 types of exploiters of mobile signaling networks. Establishing first how do we know what is malicious in terms of traffic. We then give an overview of what mobile surveillance companies do, before going into detail on how location tracking is done via SS7, Diameter and Simjacker attacks, by showing real-life examples.
We finally make a projection for 5G, and how surveillance companies will target 5G core networks as they are deployed globally over the next few years.
Content:
- 3 Types of exploiters of mobile signaling networks
- How do we know what is malicious?
- What do mobile surveillance companies do
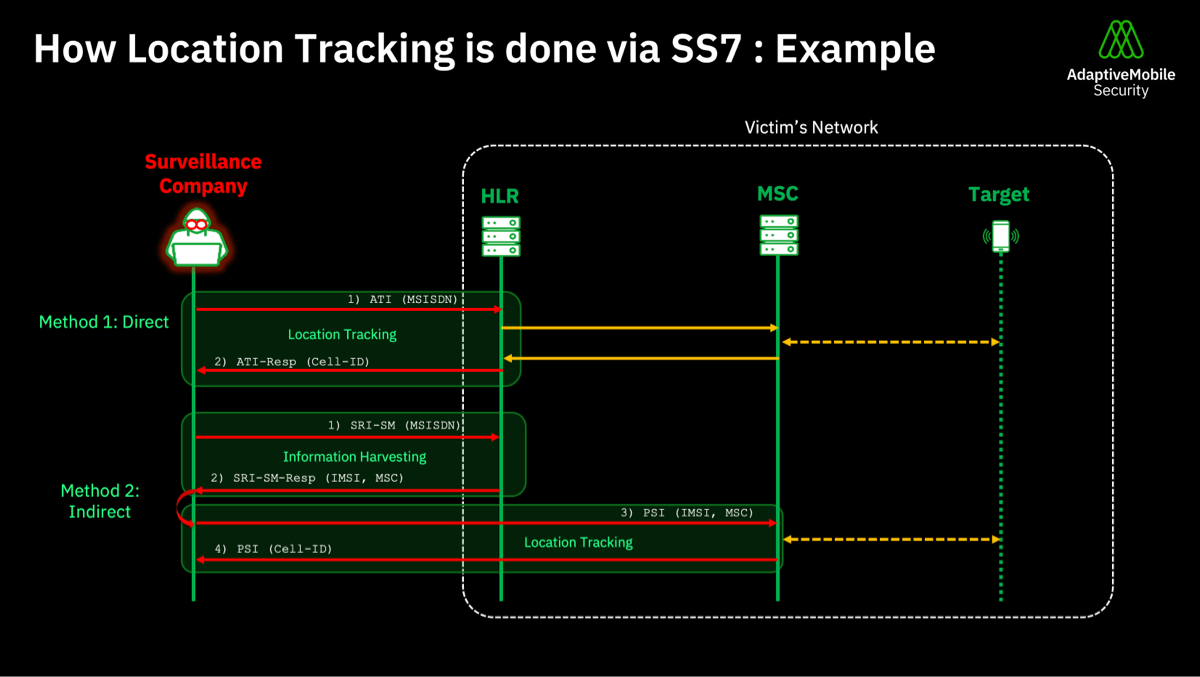
- How location tracking is done via SS7: example
- SS7 location tracking command ‘toolbox’ – attacker pros and cons
- Complexity/info needed v possibility to be blocked: SS7
- Sample real-life attempted attack – SS7
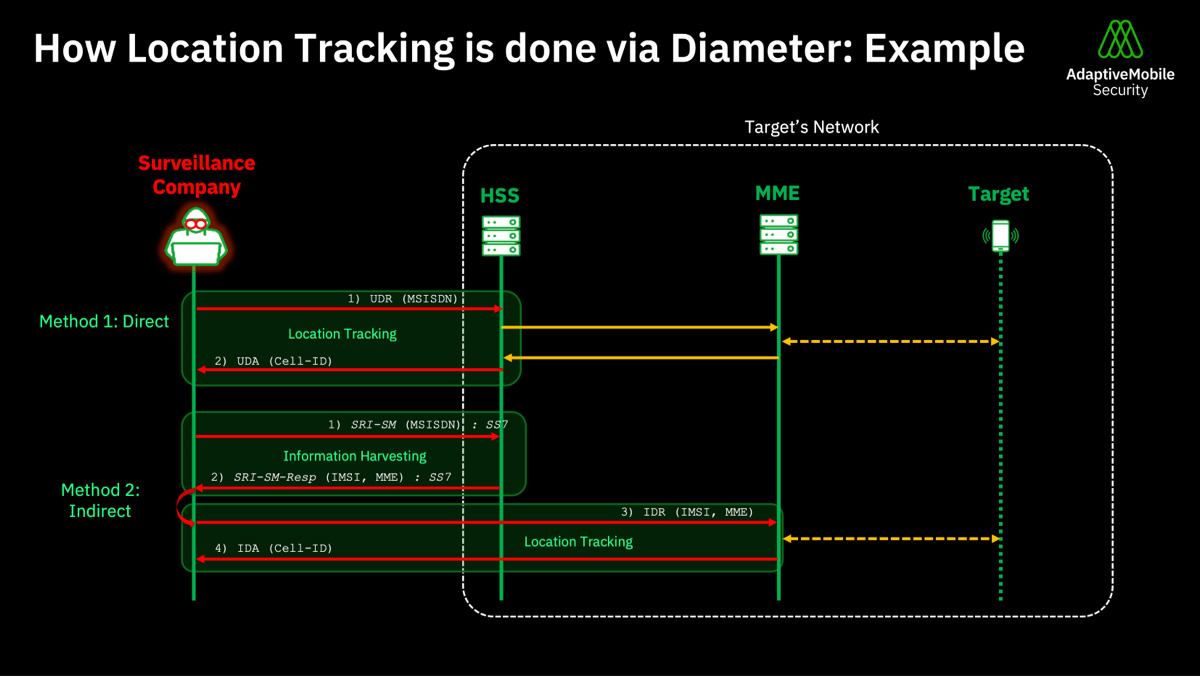
- How location tracking is done via Diameter: example
- SS7 location tracking command ‘toolbox’ – attacker pros and cons
- Complexity v possibility to be blocked: SS7 and Diameter
- Sample real-life attempted attack – Diameter
- Simjacker
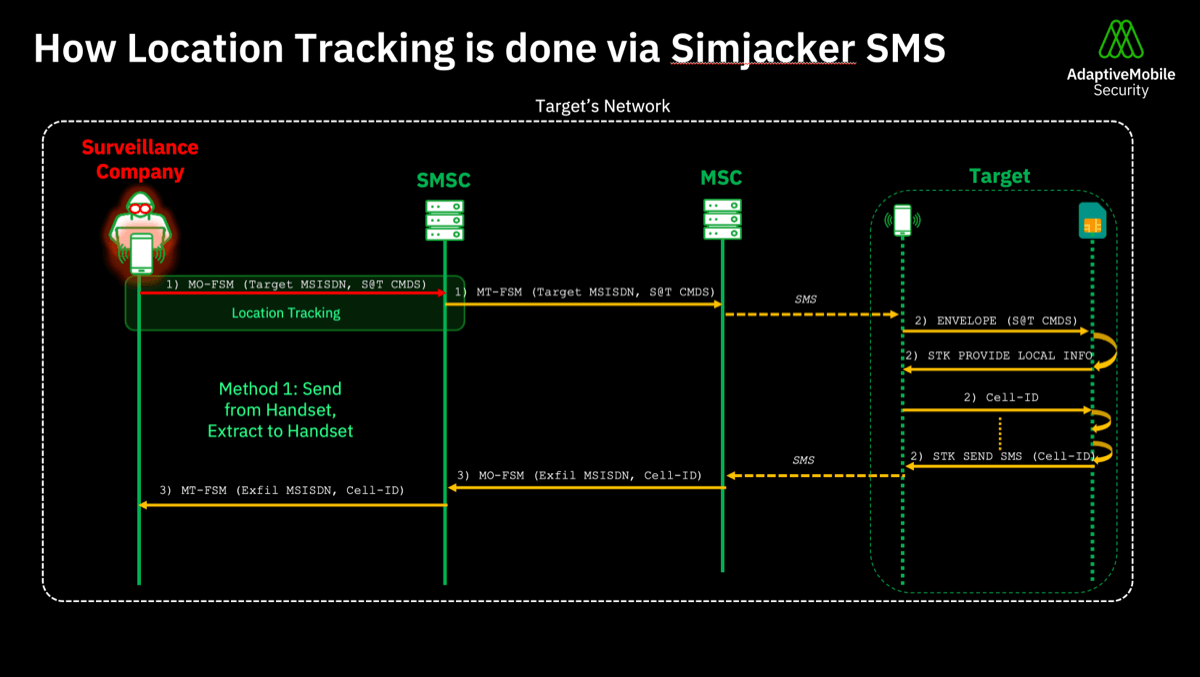
- How location tracking is done via Simjacker SMS
- Simjacker location tracking commands ‘toolbox’ – attacker pros and cons
- Complexity v possibility to be blocked: SS7, Diameter, Simjacker
- Sample real-life attempted attack – Simjacker
- Distribution of location tracking commands
- Trends of SS7 location tracking commands over time
- How do these surveillance companies gain access?
- 5G and mobile surveillance companies
- 5G location tracking commands ‘toolbox’ – attacker pros and cons
- Complexity v possibility to be blocked: SS7, Diameter, Simjacker & 5G





